
By National Cyber Security Alliance, Special for USDR
In an increasingly technology-oriented world, cybercrime has become all too common for both consumers and businesses. Internet crime takes many forms and includes everything from large-scale data breaches to consumer issues like identity theft and cyberstalking to widespread scams and ransomware. In the third week of National Cyber Security Awareness Month (NCSAM), the National Cyber Security Alliance (NCSA), the U.S. Department of Homeland Security (DHS) and their industry, government and nonprofit partners are highlighting the different types of online crime and how people and businesses can better protect themselves.
“As cybercriminals sharpen their hacking skills, we must take stronger precautions to protect our information and all of our connected devices,” said Michael Kaiser, executive director of NCSA. “There are simple things everyone can do to better safeguard their key accounts, devices and apps, like keeping software up to date, turning on strong authentication and exercising extreme caution when reading messages containing links or requests for information.”
Tech support scams make up one of the most common forms of cybercrime, and many companies providing technology products and services find themselves targeted by cybercriminals. Microsoft’s new survey and infographic on these crimes share the following eye-opening findings:
- One in five consumers surveyed admitted to continuing a potential fraudulent interaction when experiencing a tech support scam (e.g., downloaded software, visited a scam website, gave a fraudster remote access to their device or provided credit card information or other form of payment).
- Nearly 1 in 10 have lost money to a tech support scam.
- Of those who had continued with a fraudulent interaction, 17 percent were older than 55 and 34 percent were between the ages of 36 and 54.
- Fifty percent of those who continued the interaction were millennials (ages 18-34).
“Tech support scams are on the rise around the world and demand urgent attention from law enforcement, private industry and individual consumers,” said Courtney Gregoire, senior attorney at Microsoft’s Digital Crimes Unit. “According to a recent survey from Microsoft, two out three people have experienced a tech support scam in the past year, with many falling victim and placing their computers and personal information at risk.1 Our aim is to make a safer digital experience for everyone, and we are excited to partner with the National Cybersecurity Alliance to help educate people on how to identify, avoid, and report these kind of scams.”
Microsoft’s blog post on the survey provides valuable information and tips for spotting and fighting scams.
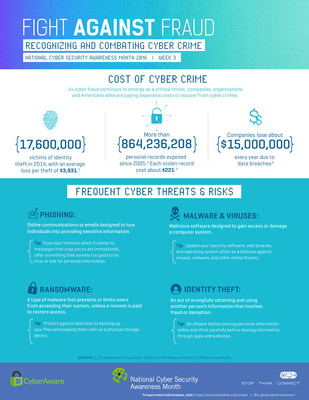
In addition to the rise in tech support-related and other scams, identity theft is a key concern for many – in fact, a 2016 NCSA survey cosponsored by Microsoft revealed that preventing identity theft was the top online safety topic both teens and parents of teens would like to learn more about.2 The Identity Theft Resource Center’s (ITRC’s) 2016 Identity Theft: The Aftermath study3, which surveyed victims of identity theft in 2015, revealed the following:
- The accounts most commonly taken over by thieves included email (11%), payment services (10%), social media (9%) and online banking (8%). Additional compromised account types include online medical portals (5%), health trackers (2%) and gaming (2%).
- Nearly a fifth of survey respondents reported significant repercussions when their online accounts were taken over, including job loss (24%) and reputational damage among friends (61%) and colleagues (31%).
- Of the respondents who identified experiencing criminal identity theft issues, 30 percent found themselves in need of state government assistance programs to overcome the financial impact of identity theft.
“Identity thieves can use a variety of platforms to commit their crimes, including many online platforms. This crime creates not only short-term effects for victims during the time they are remediating their cases – it creates long-term effects as well,” said ITRC President/CEO Eva Velasquez. “When we look at the sheer volume of identity theft it is easy to get lost in the number; we must not forget that behind each percentage and incident we count, there is a person whose life is being affected. This in turn affects families, communities, regions and our country as a whole.”
In recent months, ransomware attacks – the “digital kidnapping” of valuable data in which malware accesses victims’ files, locks and encrypts them, and then forces victims to pay ransom to get the files back – have grown more sophisticated and prevalent. The FBI has warned that these attacks are on the rise4, and according to Kaspersky Lab, the number of individuals attacked by crypto-ransomware increased 5.5 times from 2014/2015 (131,000) to 2015/2016 (718,000).5 These threats can be especially damaging to businesses, which may store critical organizational data, intellectual property and consumer information. “Having a backup that can restore the impacted system is a key defense that can help organizations restore normal operations quickly after being impacted by ransomware,” said Kaiser.
NCSA’s STOP. THINK. CONNECT.™ campaign recommends that both consumer and business audiences take the following steps to prevent and recover from cybercrime such as scams, identity theft and ransomware attacks:
- Lock down your login: Fortify your online accounts by enabling the strongest authentication tools available, such as biometrics, security keys or a unique one-time code through an app on your mobile device. Your usernames and passwords are not enough to protect key accounts like email, banking and social media.
- Keep all machines clean: Having the latest security software, web browser and operating system is the best defense against viruses, malware and other threats. If you have experienced cybercrime, immediately update all software on every internet-connected device. All critical software, including PCs and mobile operating systems, security software and other frequently used programs and apps, should be running the most current versions. Use security software to scan any USBs or external devices.
- Back it up: Make sure you have a recent and securely stored backup of all critical data.
- Make better passwords: A strong password is a sentence that is at least 12 characters long. Focus on positive sentences or phrases that you like to think about and are easy to remember.
- When in doubt, throw it out: Links in email, tweets, posts and online advertising are often how cybercriminals try to steal your personal information. Even if you know the source, if something looks suspicious, delete it.
- Help the authorities fight cybercrime: Report stolen finances or identities and other cybercrime to the FBI Internet Crime Complaint Center (IC3), the ITRC, the Federal Trade Commission (FTC) and/or your local law enforcement or state attorney general as appropriate.
While many cybercrime discussions focus on identity theft and scams, cybercrime can also include online domestic violence, stalking and harassment. The National Center for Victims of Crime and the U.S. Department of Justice’s Office for Victims of Crime have resources for victims of domestic violence, stalking, sexual assault, financial crimes and other offenses. Additionally, see NCSA’s pages on cyberbullying and harassment and identity theft and fraud for more resources andinformation.
For more on NCSAM Week 3, check out our infographic and video overview of theweek.
NCSAM Week 3 Resources for Recognizing and Fighting Cybercrime
Fighting the growing issue of cybercrime requires a high level of collaboration among law enforcement, government agencies, the private sector and the general public. If you suspect that you have become a victim, NCSA recommends contacting law enforcement. The following lists different organizations that specialize in combating online crime:
- DHS Resources:
- Immigration and Customs Enforcement Homeland Security Investigations Cyber Crimes Center (C3): C3 provides technical services and training to help federal, state and local law enforcement agencies across the country and international partners in their cyber and technical investigations.
- U.S. Secret Service Electronic Crimes Task Force (ECTF): The ECTF works to identify and locate international cybercriminals and leverages partnerships with academia and the private sector to prevent, detect and investigate electronic crimes, including potential terrorist attacks against critical infrastructure and financial payment systems.
- NCSA ID Theft, Fraud & Victims of Cybercrime Tips: If you’re a victim of cybercrime, you need to know what to do and respond quickly. NCSA provides tips for reporting and preventing several types of cybercrime.
- Council of Better Business Bureaus (BBB) Scam Tracker: Spot a business or offer that sounds like an illegal scheme or fraud? Tell the BBB about it to help them investigate and warn others by reporting what you know.
- FTC Complaint Assistant: Complaints from consumers help the Federal Trade Commission detect patterns of fraud and abuse. Report complaints related to identity theft, scams, unwanted telemarketing or spam, phones, internet services, education, jobs, credit and debt and more.
- FBI IC3: The IC3, a partnership between the FBI, the National White Collar Crime Center and the Bureau of Justice Assistance, accepts online crime complaints from victims and/or third parties.
- ITRC: The ITRC is a nonprofit organization established to support victims of identity theft in resolving their cases and to broaden public education and awareness in the understanding of identity theft, data breaches, cybersecurity, scams/fraud and privacy issues.
- Logical Operations Resources:
- CyberSAFE Readiness Test: End-users play a critical role in protecting their organization’s data, but they are often the weakest link in the security chain due to lack of awareness of potential threats. The CyberSAFE Readiness Test is a complimentary tool that can be used to measure the extent to which employees can recognize and avoid common cyber threats like phishing, malware, and non-secure websites.
- Complimentary NCSAM Kits: Help keep cybersecurity awareness front and center in your organization with a complimentary NCSAM kit. The kits, created by Logical Operations, include cybersecurity PSAs to hang up at your office, tent cards to place in breakrooms, web cam privacy covers and emails you can send to your employees.
- Morrison & Foerster Op-Ed – Stop victim shaming in cyber attacks: Miriam Wugmeister, global co-chair of Morrison & Foerster’s Privacy + Data Security practice, published an op-ed in The Hill regarding the dangers of victim shaming and the need for increased cooperation between law enforcement, regulators, and the private sector following a cyber attack. In her piece, Ms. Wugmeister notes that, “in the aftermath of a data security breach – unlike physical assaults or property crimes – a company is likely to be treated as a suspect, not a victim.” With attackers growing ever more sophisticated, our only hope of stemming the tide is increased collaboration, not finger pointing and passing blame.
- The No More Ransom Project: NoMoreRansom.org aims to provide helpful online resources for victims of ransomware. Users can find information on what ransomware is, how it works and how to protect themselves. The portal provides users with tools that may help recover data that has been locked by cybercriminals.
Upcoming NCSAMEvents
- NCSAM Week 3 Keystone Event, Wednesday, Oct. 19, 9 a.m. – 1 p.m. (PDT), Kenneth Hahn Hall of Administration, Los Angeles, CA: The City and County of Los Angeles are hosting a keystone event as part of NCSAM week 3; panel discussions will address recognizing and combating cybercrime as a community and cybersecurity for small businesses. Learn more and register for the event here.
- The Passcode Cup, Friday, Oct. 21, 11:30 a.m. – 5:15 p.m. (EDT), Impact Hub DC, Washington, D.C.: The Passcode Cup is a free, team based capture-the-flag competition with challenges based on reverse-engineering, forensics, web security, cryptography, binary exploitation and simulated industrial control systems. It is organized by Passcode, sponsored by Northrop Grumman and (ISC)² and run with the generous help of Cal Poly Pomona, Uber and Facebook. Learn more and register here
- Closing the Threat Gap: Executive Perspectives on the Cybersecurity Landscape, Wednesday, Oct. 26, 3:30-6:00 p.m. (EDT),Stevens Institute of Technology, Hoboken, NJ: Fasoo is partnering with NCSA, the New Jersey Technology Council and theStevens Institute of Technology to host an event featuring keynote speakers Dr. Larry Ponemon, chairman of the Ponemon Institute, and Mark Lobel, U.S. and global practice leader in PricewaterhouseCoopers’ Cyber Security and Privacy Practice. The keynotes will be followed by a panel discussion monitored by Dr. Paul Rohmeyer, associate professor of information security management and risk assessment. Learn more and register here.
- CyberFest2016 – The Future Is Now, Thursday, Oct. 27, 8 a.m. – 5 p.m. (PDT), Hilton La Jolla Torrey Pines, 10950 North Torrey Pines Road, La Jolla, CA: CyberFest2016 is a gathering of cyber, infrastructure, law enforcement, InfraGuard, military and business professionals, who will explore how cyber is now so interwoven into the business fabric that should it “break,” business as we currently know it will no longer exist. Learn more and register here.
- Future of Authentication Policy Day, Thursday, Oct. 27, 1-4 p.m. (EDT), Google DC Offices, Washington, D.C.: The FIDO Alliance, the Electronic Transactions Association and NCSA will jointly host an event in support of NCSAM to highlight the importance of strong authentication, explore the evolution of the authentication market and discuss its impact on the policy and regulatory landscape. Learn more and register to attend here.
- Security of Things Forum // Washington, 8 a.m. – 5 p.m. (EDT), JW Marriott, Washington, D.C.: The rapid spread of the Internet of Things inside America’s most critical industries is raising a new set of security concerns. Created by The Security Ledger and Passcode, this daylong event will bring together policymakers, experts and executives to explore the myriad risks associated with the industrial IoT and the best and most promising solutions for securing these new technologies. Learn more and register here.
- NCSAM Week 5 Keystone Event, Monday, Oct. 31, 9:45 a.m. – 12:00 p.m. (EDT), Jack Morton Auditorium, School of Media and Public Affairs, The George Washington University, Washington, D.C.: The George Washington University’s (GW’s) Division of Information Technology is hosting a keystone event to educate the community on the importance of cybersecurity and discuss public-private partnerships toward critical infrastructure protection and cybersecurity careers, scholarships and community programs. The event will feature remarks from representatives of GW, DHS, Cisco, Tripwire and NCSA. Learn more and RSVP here.
Throughout the month, you can follow the NCSAM conversation on social media using the hashtag #CyberAware (and tagging your own posts with #CyberAware, too!). Additionally, @STOPTHNKCONNECT is hosting weekly Twitter chats throughout October to discuss different topics and trends in cybersecurity. Tune in each Thursday through Nov. 3 at 3 p.m. EDT to join the conversation, and visit theSTOP. THINK. CONNECT.™, website for the full chat schedule. NCSA has created sample social media posts, infographics, posters, memes and more that encourage organizations and individuals to show their support for NCSAM and that can be downloaded and shared. You can also get the latest resources as they are available by registering as a NCSAM Champion. Finally, check out the Stay Safe Online blog for NCSAM posts from NCSA and partners during the month of October.
About National Cyber Security Awareness Month
National Cyber Security Awareness Month (NCSAM) was created as a collaborative effort between government and industry to ensure every American has the resources they need to stay safer and more secure online. Now in its 13th year, NCSAM is co-founded and co-led by the U. S. Department of Homeland Security and the National Cyber Security Alliance, the nation’s leading nonprofit public-private partnership promoting the safe and secure use of the Internet and digital privacy. Recognized annually in October, NCSAM involves the participation of a multitude of industry leaders ‒ mobilizing individuals, small and medium-sized businesses, nonprofits, academia, multinational corporations and governments. Encouraging digital citizens around the globe to STOP.THINK. CONNECT.™,NCSAM is harnessing the collective impact of its programs and resources to increase awareness about today’s ever-evolving cybersecurity landscape. Visit the NCSAM media room to learn more.
About the National Cyber Security Alliance
The National Cyber Security Alliance (NCSA) is the nation’s leading nonprofit, public-private partnership promoting cybersecurity and privacy education and awareness. NCSA works with the U.S. Department of Homeland Security (DHS) and NCSA’s Board of Directors, which includes representatives from ADP; AT&T Services, Inc.; Bank of America; Barclays; BlackBerry Corporation; Cisco; Comcast Corporation; ESET North America; Facebook; Google; Intel Corporation; Logical Operations; Microsoft Corp.; NXP Semiconductors; PayPal; PKWARE; Raytheon; RSA, the Security Division of EMC; Salesforce; SANS Institute; Symantec and Visa Inc. NCSA’s core efforts include National Cyber Security Awareness Month (October), Data Privacy Day (January 28) and STOP. THINK. CONNECT.™, the global online safety awareness and education campaign cofounded by NCSA and the Anti Phishing Working Group, with federal government leadership from DHS. For more information on NCSA, please visit staysafeonline.org/about-us/overview/.
About STOP. THINK. CONNECT.™
STOP. THINK. CONNECT.™ is the global cybersecurity education and awareness campaign. The campaign was created by an unprecedented coalition of private companies, nonprofits and government organizations with leadership provided by the National Cyber Security Alliance (NCSA) and the Anti-Phishing Working Group (APWG). The U.S. Department of Homeland Security leads the federal engagement in the campaign. Learn how to get involved at stopthinkconnect.org.
SOURCE National Cyber Security Alliance






Leave a Reply